Vulnerability Management, Detection & Response

6x faster

200K+ vulnerabilities

60% faster

Eliminate risk

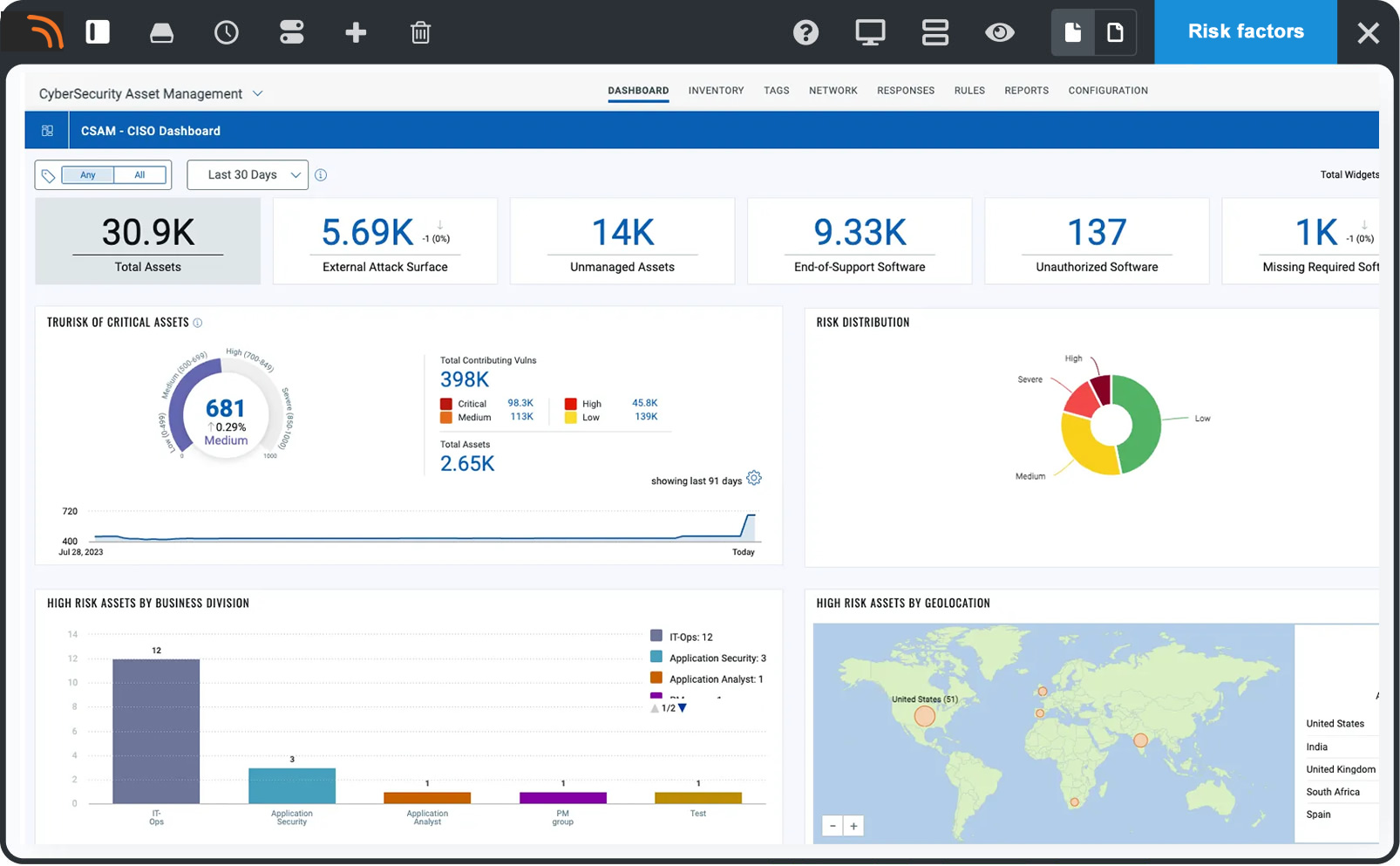
Identify assets automatically
Create automated workflows and manage them effectively so you always know about every active asset across your global hybrid-IT environment.
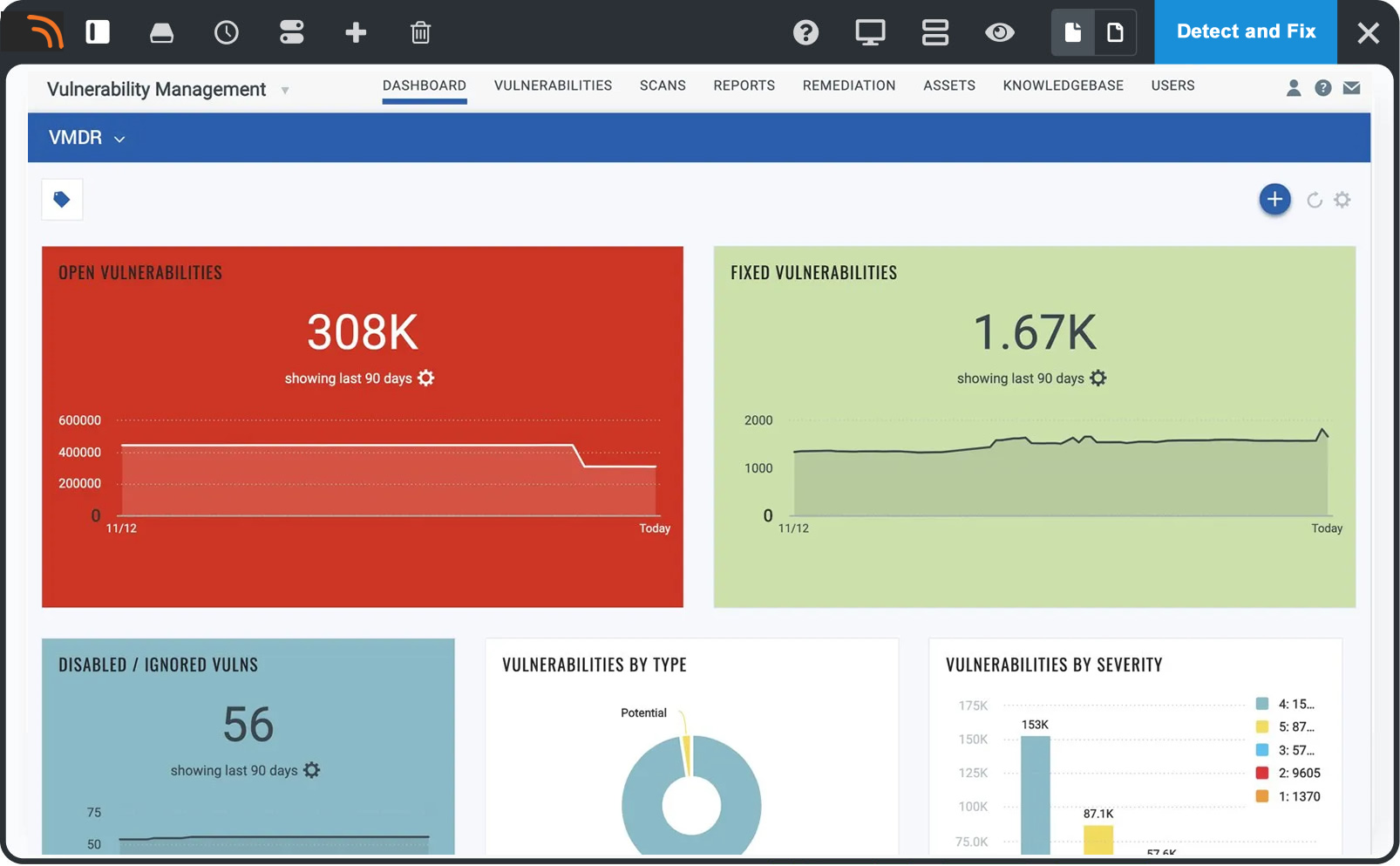
Detect vulnerabilities in real-time
Continuously detect critical vulnerabilities and misconfigurations across mobile devices, operating systems, and applications per industry standard hardening CIS benchmarks.
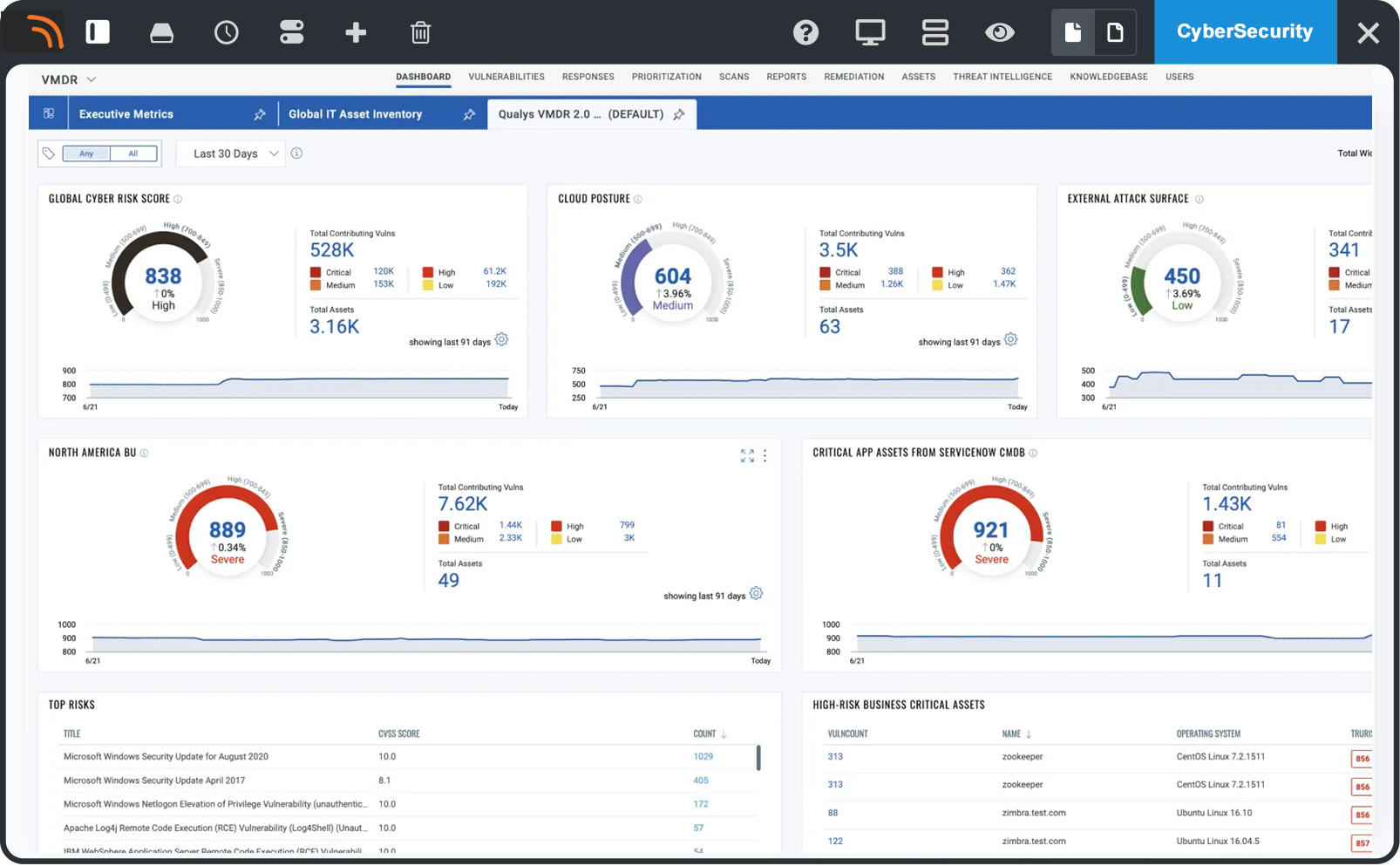
Automate & prioritize remediation
Prioritize based on evidence of exploitation in the wild and the likelihood of exploitation to quickly see which vulnerabilities, assets, and groups of assets are most at risk.
Powered by the Enterprise
TruRisk™️ Platform
Frequently Asked Questions
A virtual machine hosting environment’s main role is to provide computing resources to virtualized desktops, which can perform almost all functionalities of a traditional computer, including but not limited to running an Operating System (The V2 Cloud’s virtual machine hosting environment currently supports Windows), run applications, store data, connect to networks, and do other computing functions.
V2 Cloud’s virtual machine hosting environment also offers other advanced features like daily backups, full admin controls, easy scaling, and ransomware protection.
All of V2 Cloud’s virtual machines come with 50GB of storage included, but you can choose how much storage for each VM according to your needs.
You can also configure different cloud VMs in your network to have different storage capacities. This is useful in situations where different machines are used for different use cases (i.e., design department vs. accounting department).
V2 Cloud virtual machine hosting is designed with scalability in mind, which is important for any business or organization that wants more control over its IT resources as needed. It’s easy to upscale your storage to follow your business’s growth via just a few mouse clicks. On the other hand, with V2 Cloud, you are able to easily downsize your IT resources from your admin control console as well.
Yes, we do. If your current VMs are hosted in another environment, our technical support team can help you migrate to our environment. We provide this as a free service once you purchase one of our cloud virtual machine hosting plans.
V2 Cloud offers 24/7 free customer support via online chat, phone, and email. We will be on standby anytime you are in need of technical support. V2 Cloud’s technical support team is always available to help, whether for application migration, application installation, upgrading, or adding cloud virtual machines.
If you need more details about how to migrate your cloud virtual machine, you are welcome to contact our support team right away.
Detect and Respond